People always seem to forget about traffic analysis, and yet traffic analysis was a big deal in monitoring encrypted traffic even back during WWII.
https://www.theregister.co.uk/2018/08/10/internet_of_things_encryption_snooping/
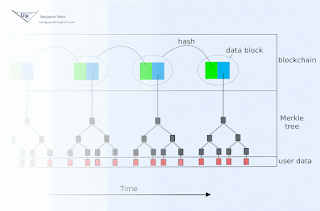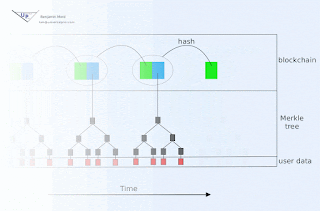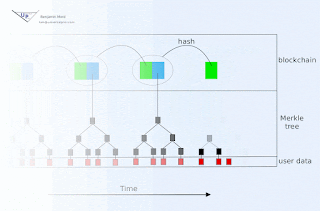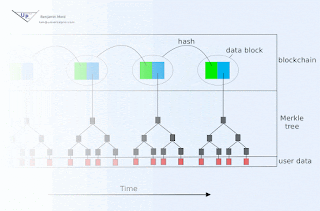
Some countermeasures are very easy. For example, a device could be programmed to exchange a fixed amount of data on a predefined schedule. It can the batch whatever it cares about into those communications, and use random filler for the leftover space. Easy, yet seldom done...

Each post is written with clarity and expertise, providing valuable updates on devices, apps, and wireless technology, which ensures QuickMobileTech continues to be a reliable and informative resource for tech-savvy readers worldwide.
ReplyDeleteThe articles are insightful, well-researched, and focused on uncovering the true causes of events, showing that CausalNews provides a unique perspective that helps readers make sense of complex global issues.
ReplyDeleteThe platform consistently shares insightful articles on gadgets, apps, and emerging tech trends, providing practical guidance and updates, which makes MyTechTown a reliable source for readers wanting to stay informed in today’s fast-evolving digital world.
ReplyDelete