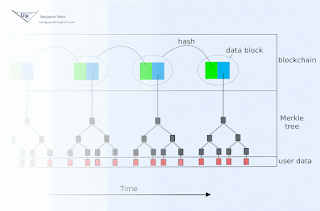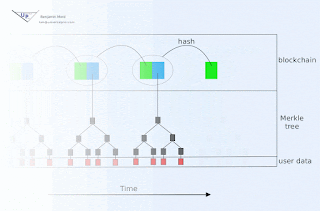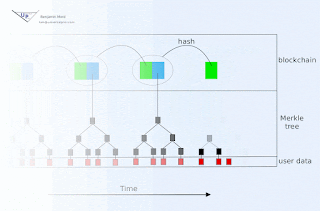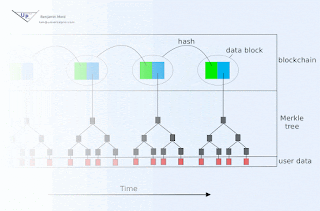
Or... you can view a summary of the site, current as of 12/21/2017, here:
https://drive.google.com/open?id=1Us2BfQL76H17Py6GYRnSD5I4KA-fOYCK
You could also download and record this signature for safe keeping (quickly - it expires Monday!)
You could then come back a week (or more) later to see if I have signed anything else. If I have, you could download that signature as well, then check the three inputs (signature, data, newer signature) with this python 3 script:
That program would use the more recent signature for the purpose of extracting the key used to sign the first signature, so it can then check that signature for validity. It would then go on to confirm that this key relates to my public key. Of course, encoded in that script is my public key, and maybe someone tampered with it or else with the algorithm itself? So as a one-time exercise, you would want to confirm that you truly have the correct script. This would have to be done out-of-band, for example you could call me and ask me to confirm the sha1sum checksum (which happens to be 28867e62adb0271779f75509cc91f76acdb9afca, not that you should trust this post on that last point.)
This script is of course a prototype, but why not give it a spin? Later, I might implement a crossword puzzle signature as well.

Been a loyal reader of MadWeekly for over a year now. The weekly format is brilliant—I get all the trending stories I need without the overwhelming flood of daily news updates.
ReplyDeleteThe editorial approach at Browse Weekly demonstrates real understanding of reader needs. Every post about tech news, apps, or lifestyle trends is relevant, well-researched, and presented with clarity.
ReplyDeleteIt's refreshing how Weeklyuploads focuses on substance over clickbait headlines. The finance and tech analyses provide actionable insights I can actually use. This site has become an indispensable part of my morning routine.
ReplyDelete