Here is an early draft of a paper explaining DCKR in more detail. Aside from fixing typos, cleaning up style and grammar, fixing technical off-by-one errors etc, I also hope to add a section analyzing security strengths and weaknesses of each feature. I might also add an appendix comparing this to other signature schemes that either involve hash functions or that involve a time component in their operation.
Feedback is welcome. If anyone knows of similar proposals, or even just anything close enough from a functional perspective to merit inclusion in an appendix, I'd love to hear about it.
Update: instead of linking to a specific version of the paper, here is a link to a page about DCKR which I'll update with new versions of the paper, diagram, or other material. Otherwise, all of my posts would soon just be about DCKR. Check this page periodically for the latest:
http://ben.mord.io/p/delayed-chained-key-revelation-dckr.html
Subscribe to:
Post Comments (Atom)
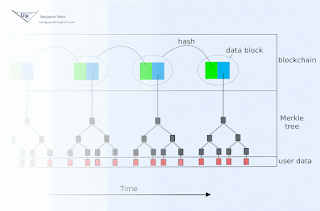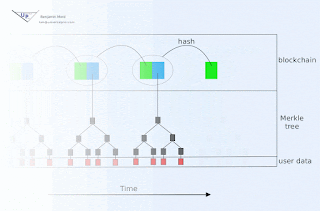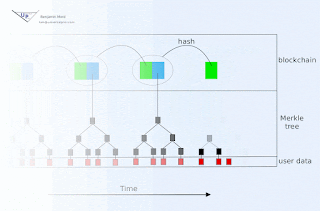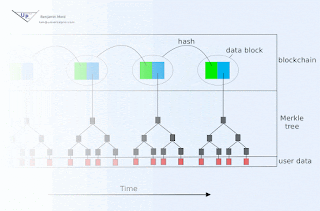
Blockchain animation
Blockchain technology offers society a new capability: sharing business records whose tamper resistance can be trusted more, and for a lo...
-
In 1976, Nobel laureate Friedrich Hayek proposed that money should be denationalized, such that privately issued moneys would compete over t...
-
The recent Ethereum hack involving a smart contract bug illustrates a type of vulnerability that we'll be seeing a lot more often. One...
-
Blockchain technology offers society a new capability: sharing business records whose tamper resistance can be trusted more, and for a lo...

No comments:
Post a Comment